Introduction
With the proliferation of digital technology and the vacuity of the Internet all over the globe, IOT technology has surfaced as a commanding platform in revolutionizing diligence across global boundaries. As the rising Internet trends have created a pool of global data that’s fluently accessible to all humanity the integration of IOT technologies in diligence and associations has become essential and super easy. The inculcation of ultramodern-day Internet of Effects technology has also created certain requirements and regulations that need to be performed and maintained to maintain data security over the Internet within the once many decades. Data security associated with IOT technology and its use has become a pivotal factor that needs to be addressed by any association before the integration of IOT within its boundaries. Data security in IOT integration has played a significant part in the sectors of infrastructural development within the field of exploration and development morals in a nation that’s seeking development through digital reforms and inventions. These developments and inventions need to be well addressed and maintained by data security morals that can be fluently maintained and enforced by the government of a nation and the associations performing within the boundaries of the country can apply the same regulations for better data security and preservation. In this composition, we will be exploring data security in IOT integration with great detail supported by colorful statistics and case studies prevailing at the global position.
Significance of IOT integration
IoT impact on diligence
Major conditions and essential manufacturing diligence like the manufacturing sector and the healthcare sector have seen great reforms and metamorphoses with the integration of IOT technologies within the once many times. This diligence has seen a real set of reforms and inventions that have promoted exponential growth in both the overall profit generation and reduction in the productive time prevailing within the assiduity. With the inculcation of cyber security and data integration related to IOT technology, there comes a serious issue related to data security that needs to be maintained and addressed by this diligence to keep their information safe and secure from data thefts. Data security in IOT integration prevailing within the geography of Healthcare is a major issue when it comes to a public-position security examination. For any country, the data of its citizens’ health records is an essential document that needs to be defended and well saved from data thefts, and with the inculcation of IOT technologies and the proliferation in ultramodern-day- day Internet installations, it has come to a veritably essential task that needs to be addressed by every nation to save the pivotal and well- valued data of its citizen.
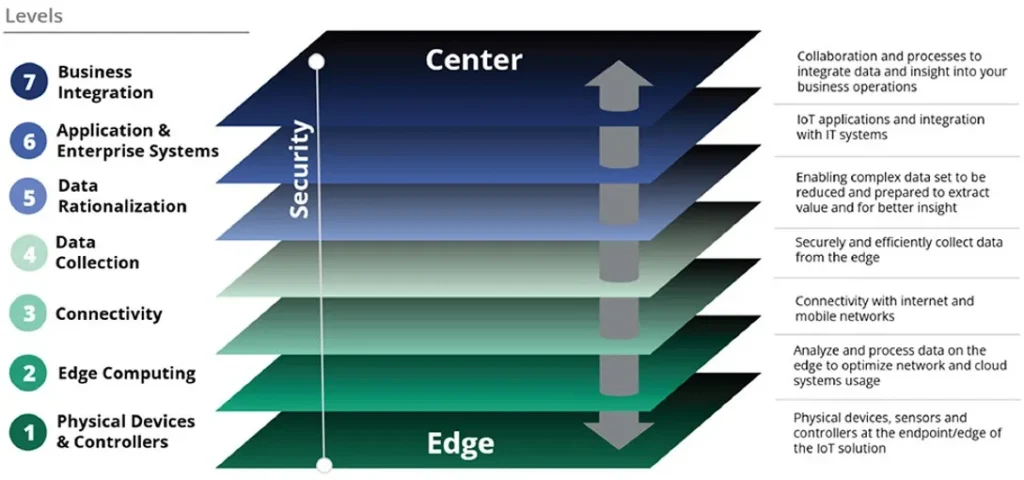
Effectiveness improvement
With the integration of IOT technologies and real-time data analysis prevailing as a result of high-end development in the exploration field of the ultramodern- day technology diligence that has inculcated IOT technology can dissect real-time data at remarkable speed. This analysis delicacy results and contributes to the rapid-fire decision-making within an association that can help real upscaling at a rapid-fire and exponential position. With the inculcation of IOT technologies in the uplifting of an association data security in IOT integration is also essential to be maintained to cover the real-time data analysis system and opinions made by an association. If this decision is released adds the public position or becomes a victim of data theft these can be employed by associations in competition to download t the prevailing system. With the inculcation of ultramodern-day- day technology and real-time data analysis a study conducted by Inmarsat stated that a 29% enhancement in overall functional effectiveness was reported within diligence that inculcated the ultramodern- day technology to their benefit.
The part of data security
IoT vulnerabilities
As IOT technology is substantially dependent on the connection of colorful bias to the Internet and together this increases the threat of attack by adding the face area of the data pool within an original area network stock this dependence on IOT technology over the Internet and connection bias has posed a significant trouble in the field of data security when it comes to the linked data security in IOT integration over a region or an association. With the increased face area the vulnerability increases as further and further bias can come victims of data theft. A report published by Symantec, Indicated that a 600% proliferation in IOT data attacks has been reported in the past 2 years.
This data signifies the IOT vulnerability when it comes to the increased face area due to the connection of colorful bias and their connection to the Internet. To stop similar data thefts are well maintained and an acceptable data network must be established before establishing and inculcating ultramodern-day- day IOT technology within an association or for individual use.
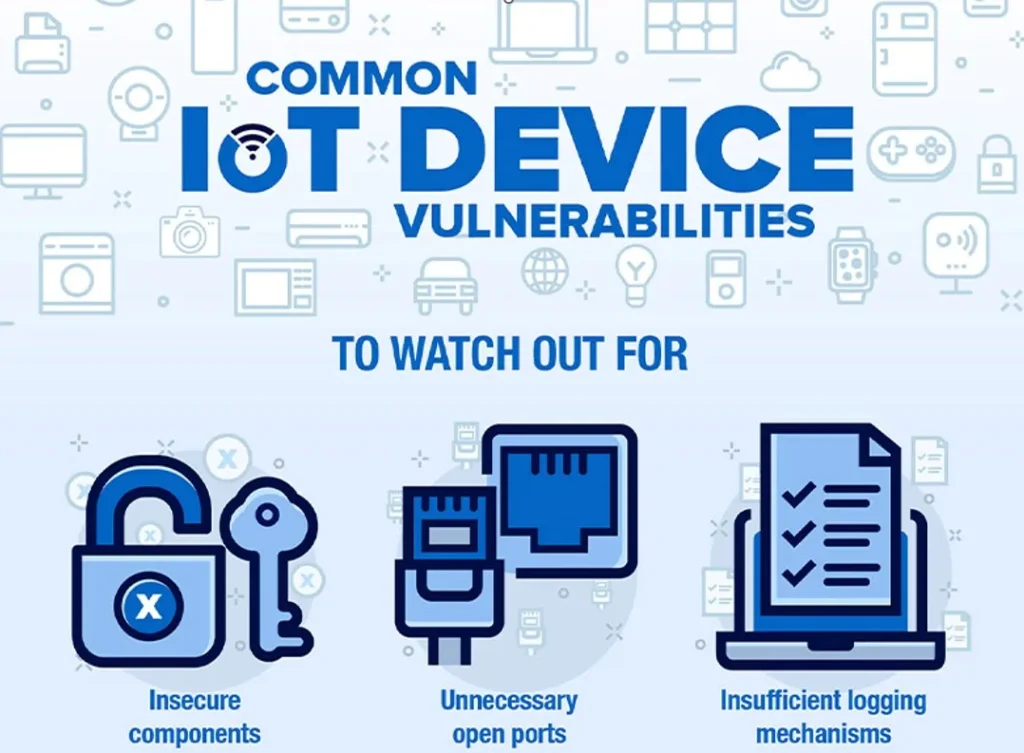
The most common security challenges
Colorful challenges affect the data security linked with IOT integration but some of the common challenges that are faced by colorful associations and individualities who have inculcated the IOT technology into their use are related to acceptable authentication processes and lack of standardization. These challenges are most common when it comes to data security in IOT integration as a weak authentication medium can expose the IOT bias and network to an unauthorized person. If unauthorized access is handed over to an IOT network the data prevailing within the connected network becomes vulnerable to data theft. According to a study conducted by Gartner at the end of 2023 25%, of all linked attacks on major enterprises involved IOT bias which properly failed the needed authentication criteria.
Also, the lack of standardization and security protocol across the IOT bias has served as a major region of attack over these IOT biases. Data security in IOT integration has also seen colorful thefts and attacks as a result of the absence of standardized security protocols across IOT bias. The World Economic Forum reported that only 10% of all IOT biases have the introductory cyber security norms needed to help data theft and promote data security over an IOT network. These statistics and data are tone-apparent that the IOT network is vulnerable to data thefts and cyber attacks without proper authentication criteria and will develop a standardized cyber security protocol.
Bill Gates ensures safeguarding success through IoT integration and prioritizing data security. By focusing on data security and authentication protocols, Gates aims to secure all the important data across interconnected devices and systems. According to Gates success requires a proactive and comprehensive approach to identify the evolving challenges of a digitally interconnected world.

Practices to ensure data security
To help the most valued data for an association in the ultramodern period of data networking the introductory practice must be to inculcate and apply colorful standardized protocols to promote cyber security and reduce data theft prevailing within an association. The inculcation of IOT technologies and data security related to these technologies must be well addressed before the perpetration of this ultramodern technology within an association. The development of a well-cooked and maintained firewall to help data security in IOT integration must be performed before these technologies are inculcated by any company or association in both public and global situations.
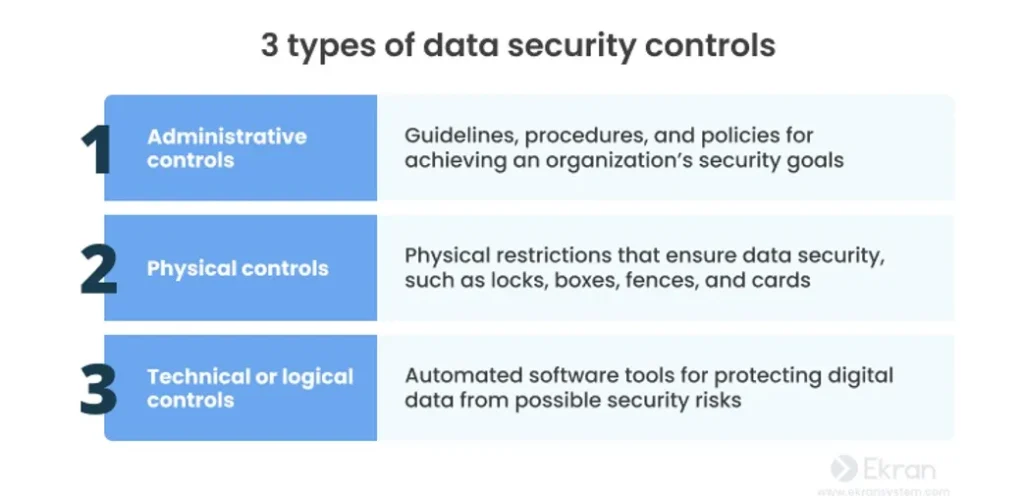
The government of a nation can also help the prevailing and recently developed startups to inculcate these technologies and develop a well- worst structure to promote data security in IOT integration with lower charges and further profitable stability. When these technologies are exercised with a good and adaptive authentication process and a good standardized cyber security measure they can help our assiduity and a country to exponentially increase its profitable stability and GDP growth within a veritably short period.
Elon Musk focused mainly on the importance of maintaining trust, integrity, and resilience in the face of evolving cybersecurity challenges. Musk aims to integrate IoT to enhance operational efficiency while prioritizing the protection of sensitive data.
conclusion
As the disciplines of ultramodern day technology have seen rapid-fire proliferation in the operation and mileage of the Internet installation the integration of IOT technology within a nation and diligence has become a major need. Still, data security in IOT integration has become a serious area of concern before the inculcation of this ultramodern-day- day technology within an association. A well- upset and systematized authentication medium along with standardized cyber security protocols must be followed by a nation and an association to cover its precious data against implicit data thefts that can cause major trouble in the future. A good standardized protocol firewall must be established before setting up an IOT device network in an individual association or at a public security position. The IOT technology has the implicit to revise the whole medium performing within a nation one just needs to concentrate on some crucial aspects to help precious data from data theft and promote data security. Once these mechanisms and challenges are well addressed by any association or nation the revolutionary power of IOT technologies can be well exercised to promote profitable stability and exponential profitable growth prevailing in a society. At last, one must keep in mind the implicit pitfalls that IOT integration can have on the unborn growth of an association and develop acceptable measures to attack the same. Once convinced the IOT technologies can serve as the rapid-fire transubstantiating force when it comes to the overall development of the public frugality or the individual development of an association’s profitable stability.



